Safety and security must be paramount for any business that wants to protect its employees, customers, and assets from potential issues and malicious actors. Yet with more cameras and sensors than ever before, how can organizations lower their risk by quickly and efficiently analyzing the flood of images and videos at their fingertips?
The solution comes in the form of edge AI for security video analytics. Below, we’ll discuss computer vision and video analytics work together and why it’s important to perform these analyses on the edge.
Computer Vision for Security Video Analytics
Computer vision is a subfield of artificial intelligence with the goal of making computers “see” like humans do. The domain of computer vision includes object recognition, facial recognition, event detection, motion tracking, and much more.
While computer vision has been widely adopted in dozens of fields and industries, safety and security is one of the top use cases for computer vision. Here at Chooch, we’ve helped many of our clients develop computer vision solutions for their safety and security AI needs. The list of examples includes:
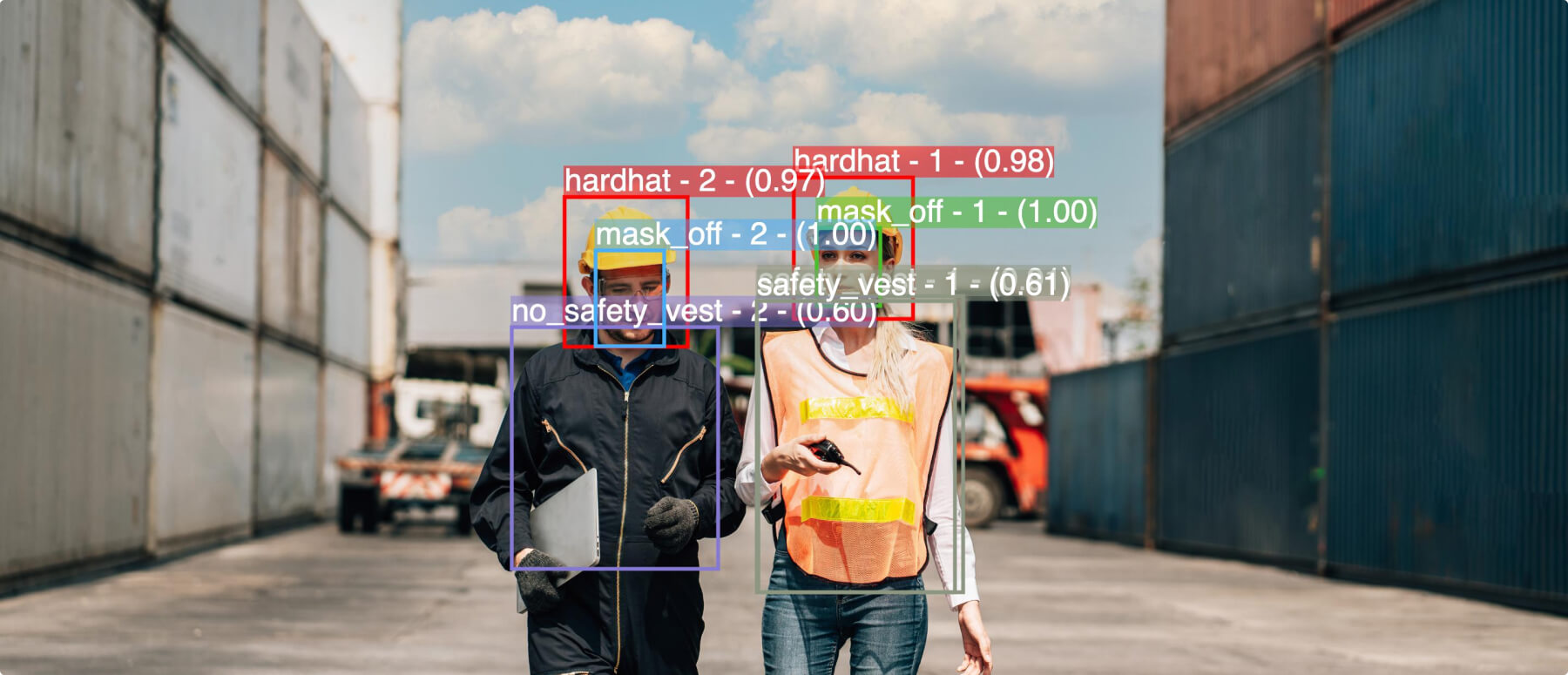
- OSHA compliance and public safety: Workplaces such as offices, restaurants, and construction sites all have their own set of health and public safety regulations that employees and customers must comply with. For example, computer vision systems can help determine whether workers are wearing protective clothing, such as hard hats or masks.
- Authentication: Certain restricted areas need to remain accessible to employees while remaining off-limits to the general public. Facial identification systems with liveness detection, supported by computer vision, can help distinguish between legitimate and illegitimate access requests.
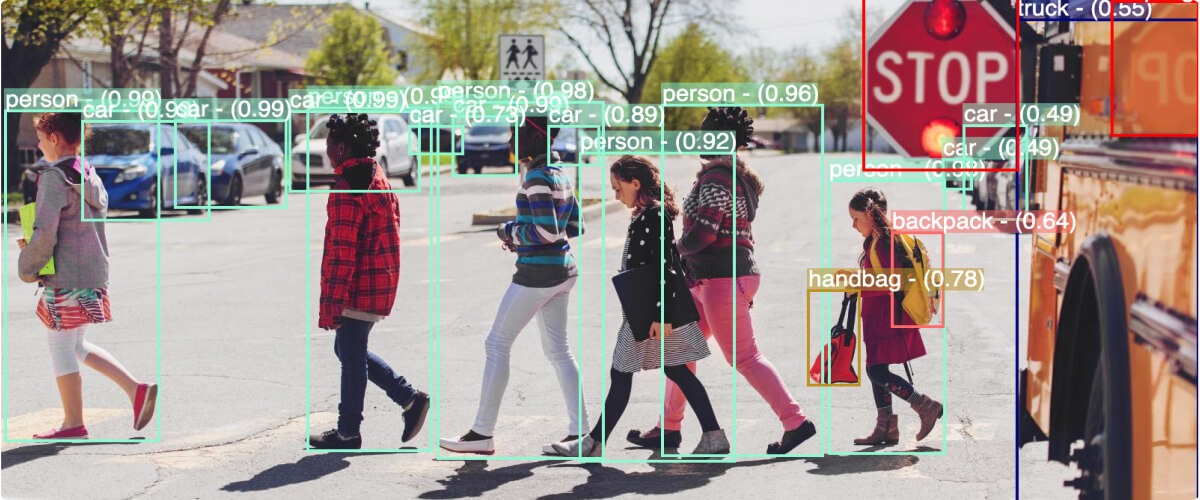
- Remote sensing: Many security cameras and sensors are located in remote areas, making it even more important to detect potential issues and risks. Computer vision can help identify suspicious vehicles, record license plates, detect breaches of a boundary or perimeter, and much more.
- Object recognition: Using cameras and thermographic sensors for infrared radiation, you can more easily identify noteworthy objects and people within just a fraction of a second, rapidly determining if they pose a security risk.
Security video analytics on the edge
While computer vision has many possible applications, few of them are as time-sensitive as safety and security. When a computer vision system identifies a potential risk to your organization, you need to take swift and decisive action.
This means, of course, that time is of the essence when performing security video analytics. Unfortunately, many computer vision systems are too slow to perform real-time analysis: instead of processing the captured images or video themselves, they upload this data to a more powerful machine in the cloud. Latency issues (waiting for data to be uploaded and analyzed) present a barrier to large-scale adoption of computer vision for safety and security AI.
That’s why edge AI is an essential development for the field of security video analytics. Edge computing is a paradigm in which data processing occurs in “edge” devices that are physically located close to the original point of capture, rather than by servers in the cloud.
While the field of edge AI is young, it’s growing rapidly as more and more businesses come to realize the benefits of edge computing. For example, Accenture predicts that by 2025, 70 percent of security surveillance cameras will come equipped with real-time monitoring and analytics capabilities, versus just 5 percent in 2018.
So how can you leverage the power of the edge for your own safety and security AI needs? Chooch has developed an edge AI platform that can deploy up to 8 models with 8,000 different classes on a single edge device, letting you identify thousands of different types of objects. Powered by NVIDIA Jetson devices, Chooch’s edge AI platform delivers results with greater than 90 percent accuracy within just a fraction of a second. Get in touch with us today for a chat about your business needs and objectives.